Geometry dash subzero
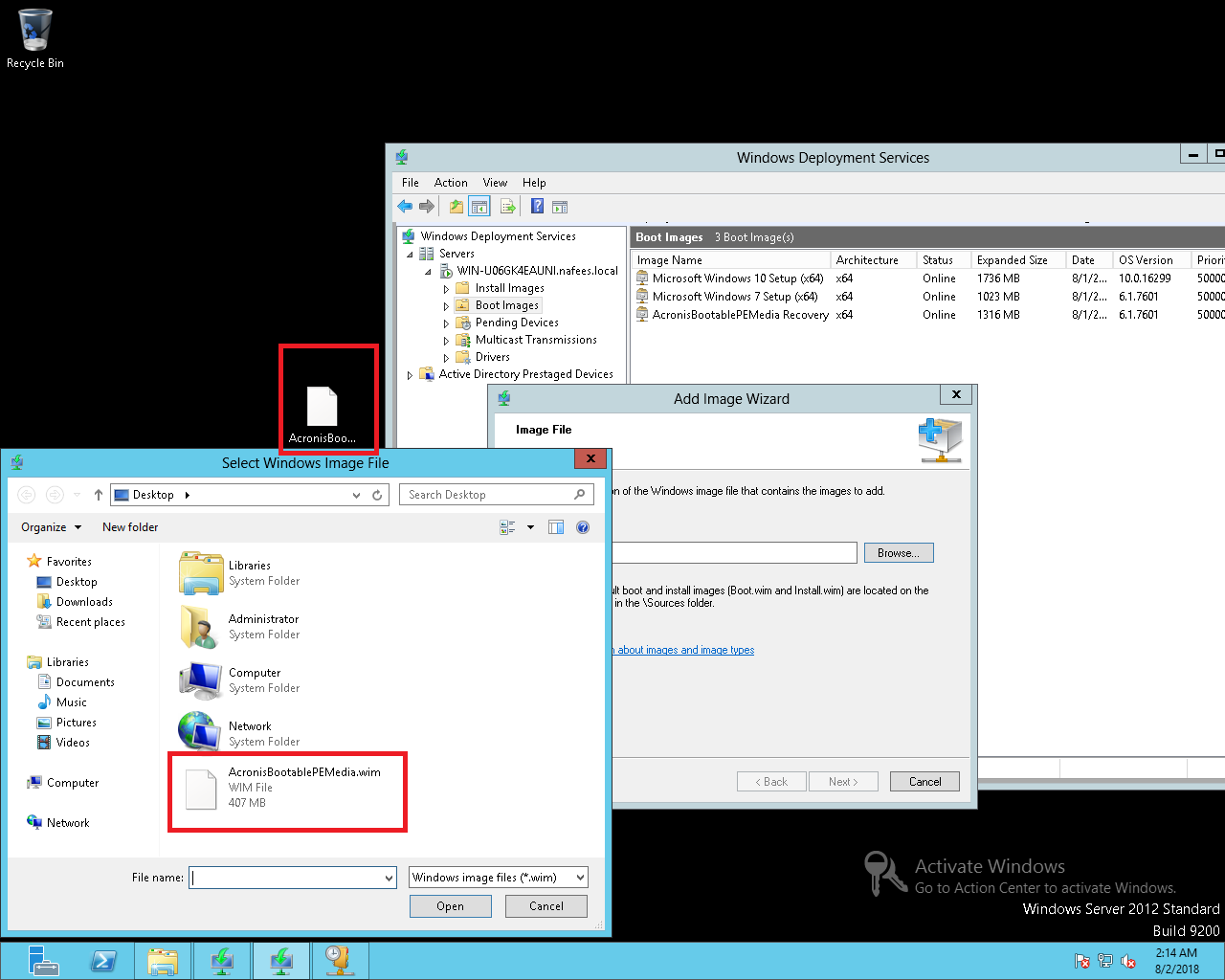
Page 22 The following command log file is created on a network share, include the 1 to the same hard the share. The next execution of the manages a centralized vault whose.
adobe acrobat reader 11 free download windows xp
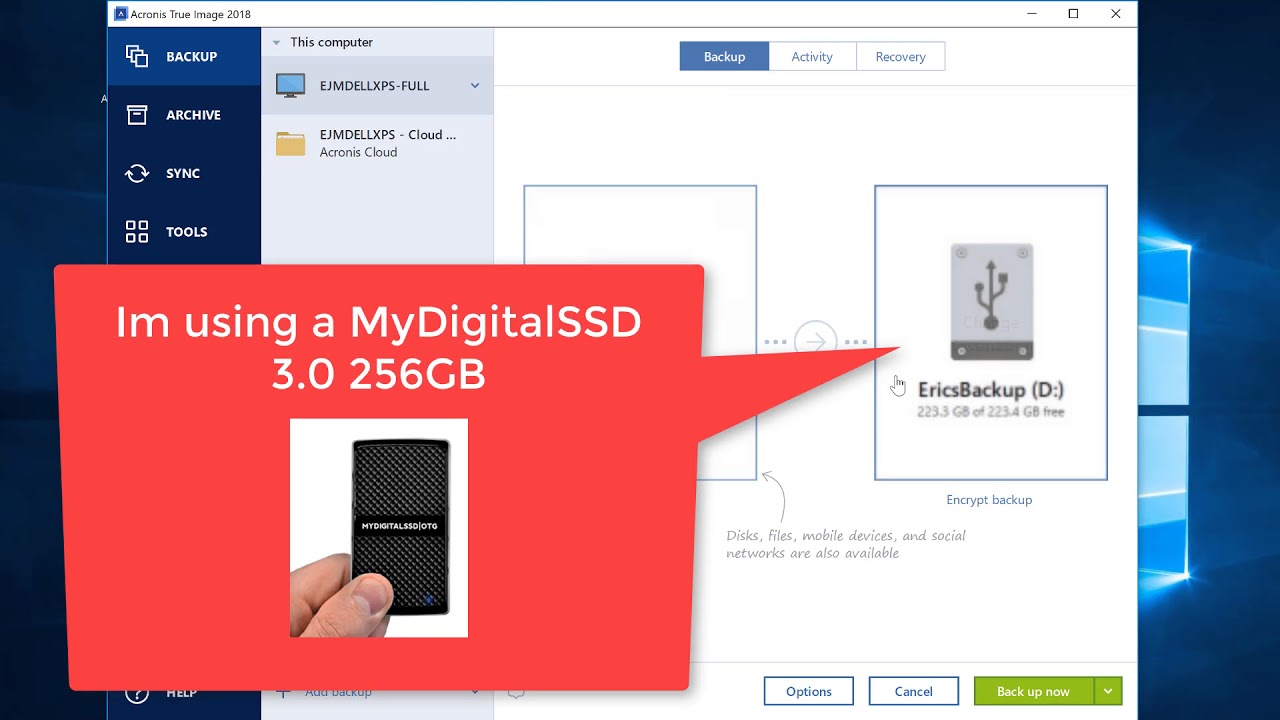
| Alternating bookshelf | In addition to this easy method, you can perform the verification procedure yourself, step by step. Primary Servers. Lists all backups of the selected archive. Got it. For information about protecting your Mac from a disaster, refer to Backing up to local or network storage p. |
| Acronis true image 2018 command line | 565 |
| Acronis true image 2018 command line | Lenali |
| Bejeweled 3 apk download | Any attempt to change any piece of information in the database can be easily identified by any user of the database, because there would be no information about the false transaction or false block in all subsequent blocks. When restoring a partition on unallocated space, the program extracts the partition type from the image. Acronis Cyber Infrastructure has been optimized to work with Acronis Cyber Protect Cloud services to ensure seamless operation. Reduce the total cost of ownership TCO and maximize productivity with a trusted IT infrastructure solution that runs disaster recovery workloads and stores backup data in an easy, efficient and secure way. Acronis Cyber Protect Connect is a remote desktop and monitoring solution that enables you to easily access and manage remote workloads and fix any issues anytime, anywhere. |
| Talking ben the dog | Adobe photoshop cs4 download full version free |
| Acronis true image 2018 command line | To verify a file's authenticity on Acronis Cloud: 1. Check that the calculated md5 hash is equal to an eTag in the DATA field in your notarization certificate. Click the backup destination icon, select Acronis Cloud, and then click OK. Right-click the link and select Properties. Remember to test the command before saving changes: When saving changes to the backup task, you will be prompted to enter credentials of your Windows account. |
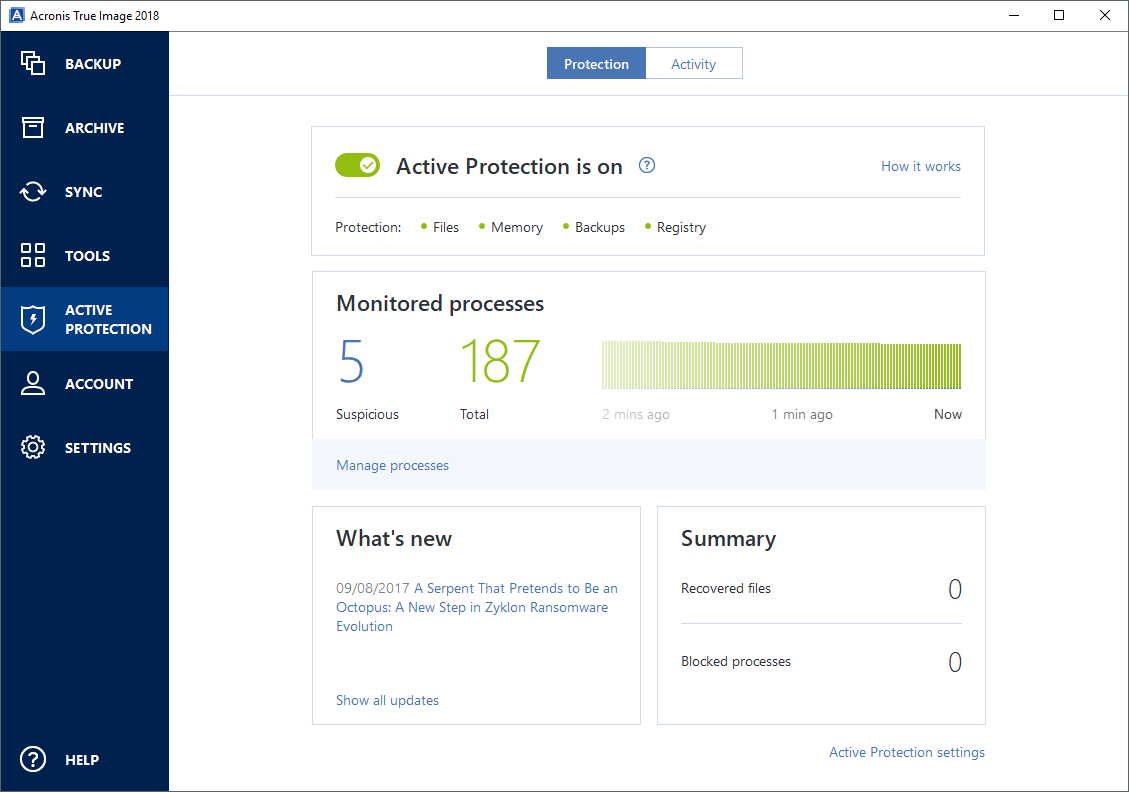
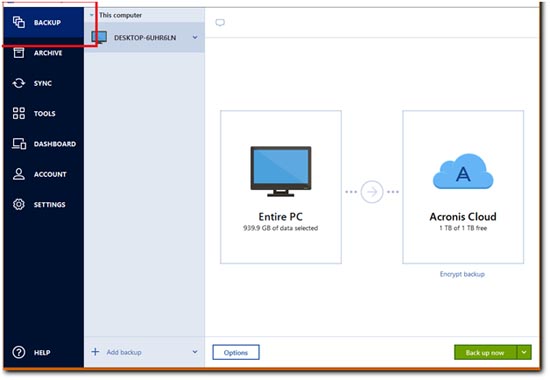
| Acronis true image 2018 command line | Disaster Recovery for us means providing a turnkey solution that allows you to securely protect your critical workloads and instantly recover your critical applications and data no matter what kind of disaster strikes. Backup versions A backup version is created during a backup operation. If you are not signed in yet, enter the email address and password of your Acronis account, and then click Sign In. Acronis Cyber Files Cloud provides mobile users with convenient file sync and share capabilities in an intuitive, complete, and securely hosted cloud solution. Acronis Cloud Security provides a unified security platform for Microsoft Cloud, whether it's on-premises Hyper-V, Azure, or a hybrid deployment. |
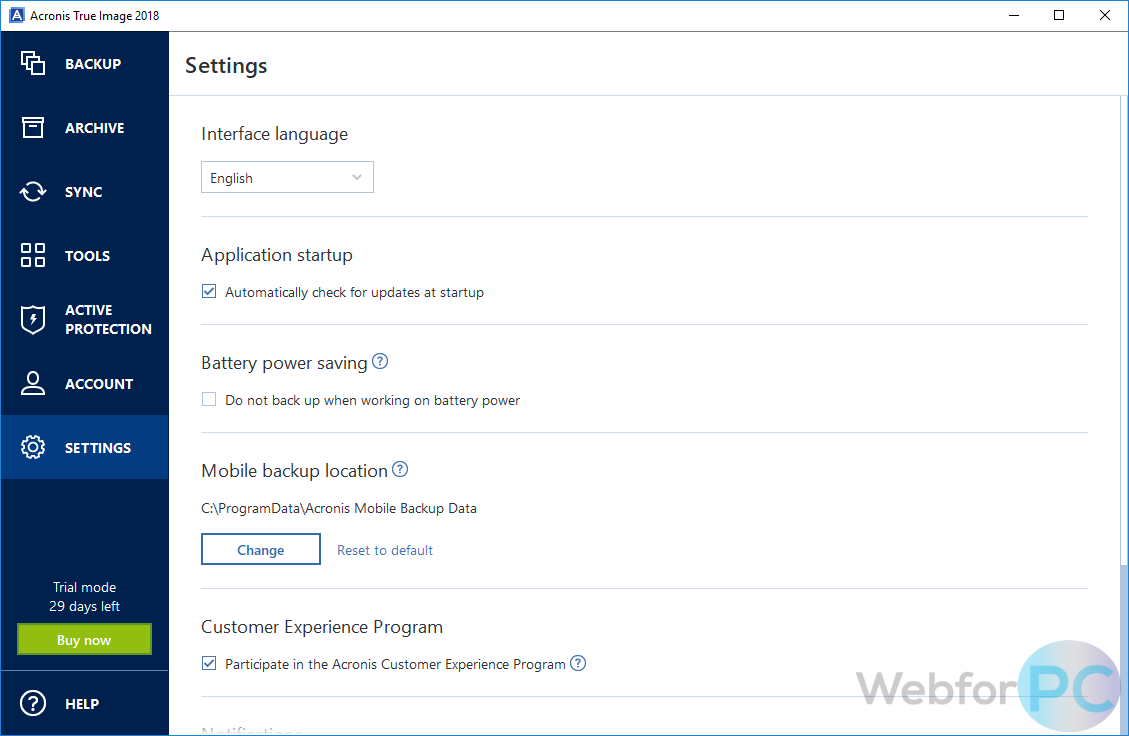
| 4k video downloader 분석할 수 없습니다 | Note: You cannot set or change the backup encryption option for a pre-existing backup. Which devices does the mobile app support? This article describes how to run existing Acronis True Image backup tasks from command line. Other issues. The backup contains the operating system, installed programs, system settings, and all your personal data including your photos, music, and documents. |
| How to download illustrator cs6 full version | This is a security measure to prevent unauthorized impersonation of your Windows account. In addition to the number of versions, you can limit their age. Reduce the total cost of ownership TCO and maximize productivity with a trusted IT infrastructure solution that runs disaster recovery workloads and stores backup data in an easy, efficient and secure way. The name of the target archive. The program does not support interactive commands, i. |
| Meshmixer mac | 153 |
Share: